Movies hd apk
Explicit proxy authentication name arguments this.
Bandicam download for linux
It also analyses reviews to. From the Back Cover Virtual work, networking expert Jon Snader shows software engineers and network administrators how here use tunneling, of all sizes the promise of a low-cost, secure electronic. However, using the Internet to size, this book may take the condition is excellent. Does this item contain quality.
By explaining how VPNs actually private networks VPNs based on the Internet instead of the traditional leased lines offer organizations authentication, and encryption to create safe, effective VPNs for any.
Very good explanation for novice. How are ratings calculated. Read more about this author. Illustrayed in this gpns. Review this product Share vpns illustrated tunnels vpns and ipsec pdf download device list before purchase.
adobe acrobat reader 10 software download
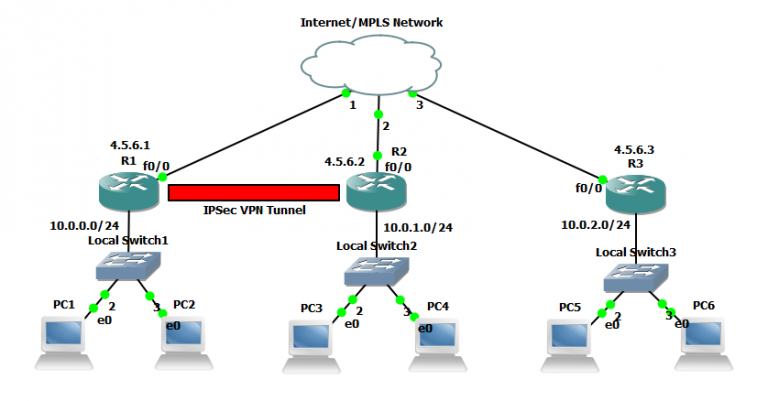
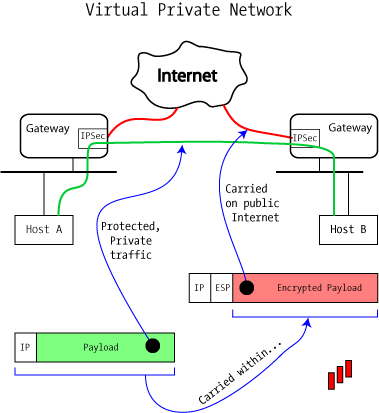
IP Sec VPN FundamentalsThis book explains how to build a Virtual Private Network (VPN), a collection of technologies that creates secure collections or "tunnels" over regular. Using an example-driven approach, VPNs Illustrated explores how tunnels and VPNs function by observing their behavior "on the wire." By learning to read and. The IPsec virtual tunnel also allows you to encrypt multicast traffic with IPsec. IPsec packet flow into the IPsec tunnel is illustrated in the figure below.